HubBroker iPaaS Security

1. INTRODUCTION
- This Security Document describes the security standards for HubBroker ApS’ iPaaS Platform.
- HubBroker ApS has made an internal security scan on the iPaaS platform.
2. DEFINITIONS
The following definitions are used in this document:
- NFS = Network File System
- SSL = Secure Socket Layer
- NW = Network
- OWASP = Open Web Application Security Project
3. IPAAS
The iPaaS is an integration platform that allows you to access and exchange data with your trading partners (customers, vendors or external organizations) and other cloud-based applications used within the company. It allows you to exchange information in the simplest possible way. It is designed for business users to self-manage their data connectivity while providing control to IT staff.
The iPaaS platform features a simple user interface to manage all adaptors and gateways for your company. The iPaaS platform reduces your integration effort and costs drastically. It is a single place to manage all your business data exchanges, where you define your business rules for exchange just once and the iPaaS platform will execute accordingly.
4. OBJECTIVE
The objective of this assessment is to assess the overall security posture of the application from a black-box perspective. This includes determining the application's ability to resist common attack patterns and identifying vulnerable areas in the internal or external interfaces that may be exploited by a malicious user.
During the internal assessment, the following tests are conducted on the iPaaS platform:
- Application Security
- Data Security
- Infrastructure and Hosting Security
5. SCOPE
The scope of this engagement is limited to components and interfaces specific to the iPaaS platform. The following URLs are considered in the scope:
- http://ipaas.hubbroker.net/
- http://ipaascrons.hubbroker.net/
6. METHODOLOGY
6.1. ASSESSMENT TYPE
HubBroker ApS has made a time-boxed manual security assessment against the iPaaS platform. This assessment involves a deep automated scan, using automated scanning tools to discover common vulnerabilities, as well as manual testing. Manual testing includes validation of all issue types covered under the automated scan as well as check for problems not typically found by automated scanners such as authentication, authorization, and business logic flaws. The results of the scan and testing have been listed as findings (please see below).
6.2. RISK ASSESSMENT METHODOLOGY
The severity assigned to each vulnerability was calculated using the NIST 800-30 r1 standard. This standard determines the risk posed by the application based on the likelihood of an attacker exploiting the vulnerability and the impact that it will have on the business.
6.2.1. LIKELIHOOD
The difficulty of exploiting the described security vulnerability includes required skill level and necessary access to visit the element susceptible to the vulnerability. The difficulty is rated with the following values:
- Critical: An attacker is almost certain to initiate the threat event.
- High: An untrained user could exploit the vulnerability or the vulnerability is very obvious and easily accessible.
- Medium: The vulnerability requires some hacking knowledge or access is restricted in some way.
- Low: Exploiting the vulnerability requires application access, significant time, resource or a specialized skillset.
- Minimal: Adversaries are highly unlikely to leverage the vulnerability.
6.2.2. IMPACT
The impact the vulnerability would have on the organization if it is exploited successfully is rated with the following values:
- Critical: The issue causes multiple severe or catastrophic effects on the organizational operations, organizational assets or other organizations.
- High: Exploitation produces severe degradation in mission capability, to the point that the organization is not able to perform primary functions, or results in damage to organizational assets.
- Medium: Threat events trigger degradation in mission capability to an extent where the application is able to perform its primary functions, but their effectiveness is reduced and there may be a damage to the organizational assets.
- Low: Successful exploitation has limited degradation in mission capability, the organization is able to perform its primary functions, but their effectiveness is noticeably reduced and may result in minor damage to the organizational assets.
- Minimal: The threat is non-existent or has a negligible adverse effect on the organizational operations or organizational assets.
7. APPLICATION SECURITY
HubBroker ApS takes security very seriously and has initiated several measures to ensure the integrity of customer data. The architecture of the iPaaS platform carefully keeps your security in mind. Since the Gateways reside in the secure HubBroker ApS’ environment, it is important that there are extensive security measures in place in order to prevent any compromise during the configuration and run-time execution of an adaptor.
7.1. COMMUNICATION SECURITY
Access to Source and Destination Gateways is through secure SSL Gateways. Access to the iPaaS platform is through a Web Application Firewall (WAF) that prevents attacks such as SQL injection, cross-site scripting, denial of service and many others. To ensure the security of data in transit, the iPaaS platform makes use of the latest and most stringent data communication security standards. All communications to and from the iPaaS platform are done using SSL encryption (SHA-256 with RSA Encryption).
7.2. ENCRYPTION SECURITY
The iPaaS platform uses AES 256 Encryption for encrypting user passwords. AES 256 is the strongest encryption available for password protection. For data at rest, the iPaaS platform uses AES 256 to encrypt and store the connection metadata in the HubBroker ApS infrastructure.
7.3. CERTIFICATES
Certain Gateways in the iPaaS platform use certificates in order to ensure security when transmitting data across a communication protocol. Gateways such as AS2, FTPS, SFTP, HTTPS and many others require the use of certificates in order to encrypt data and channels and to verify the digital signature of the application sending the data. The Certificate Component can use an existing key obtained from a certificate authority such as VeriSign or a key generated by HubBroker ApS.
7.4. PROTECTION AGAINST ATTACKS
HubBroker ApS has implemented the following techniques to prevent attackers to exploit the vulnerabilities in the iPaaS platform:
- OWASP Top 10 Vulnerabilities
- Web Application Vulnerabilities
- Operator-sided Data Leakage
- Insufficient Data Breach Response
- Insufficient Deletion of Personal Data
- Non-transparent Policies, Terms, and Conditions
- Collection of data not required for the primary purpose
- Sharing of data with third-party o Outdated Personal Data
- Missing or Insufficient Session Expiration o Insecure Data Transfer
- Follows SOC2 SSAE 16 Security Compliance Guidelines
- Runs on AWS Virtual Private Cloud
- Distributed Denial of Service (DDoS) Mitigation
7.5. LOGICAL SEPARATION OF OBJECTS
The iPaaS platform follows these guidelines to logically separate objects:
- One company's objects cannot be accessed by any other company
- Every object tagged with Company ID
- Data store schema design
- Code/logic enforces access by Company ID
- Encrypted Databases and Storage
7.6. USER AUTHENTICATION
The iPaaS platform follows these guidelines to provide secure authentication for user access:
- Admin users approve other users
- User Management console available
- Password policies
- Strong password enforced
- Password retries are limited
- Password expiry option available
- Users can be deactivated/paused before deleting
- Separate environments for separate departments
7.7. ROLE BASED SECURITY
The iPaaS platform follows these guidelines to provide role-based security:
- Admin Users
- Gives access to business users
- Manage module access to business users
- Monitor business user activity
- Admin controls what adaptors and different types of gateways are available
- Audit Trail
- Tracks history of business user actions
- Object Locking
- Prevents changes to approved objects
7.8. USER AUTHORIZATION
The iPaaS platform follows these guidelines for user authorization:
- Access to Shared adaptors is only allowed to authorized customers or partners
- The system tracks all those who are authorized
- Admin has the ability to revoke access
7.9. FINDINGS
8. DATA SECURITY
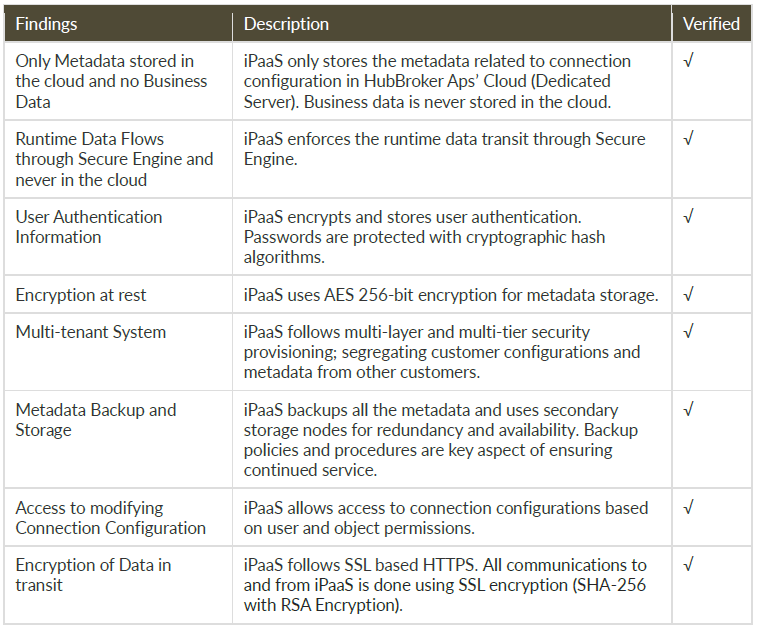
The iPaaS platform is engineered to optimize interoperability of applications and facilitate your integration processes. HubBroker ApS is saving your data in our data center, unless specifically configured not to do so. You can also make additional archiving processes in the iPaaS platform.
8.1. HOSTED METADATA
For Gateways deployed in our data center, you will have all the security that our data center infrastructure provides in order to ensure that your metadata resides in a secure system. These data centers provide the highest level of SaaS security available. This will ensure that all your metadata for your hosted Gateways is fully secure and only accessible by your account. The iPaaS Secure Bridge and Engine helps you maintain confidentiality and privacy of your data by allowing you to connect to your internal applications securely. It can also help moving data processing to your own premises, if required.
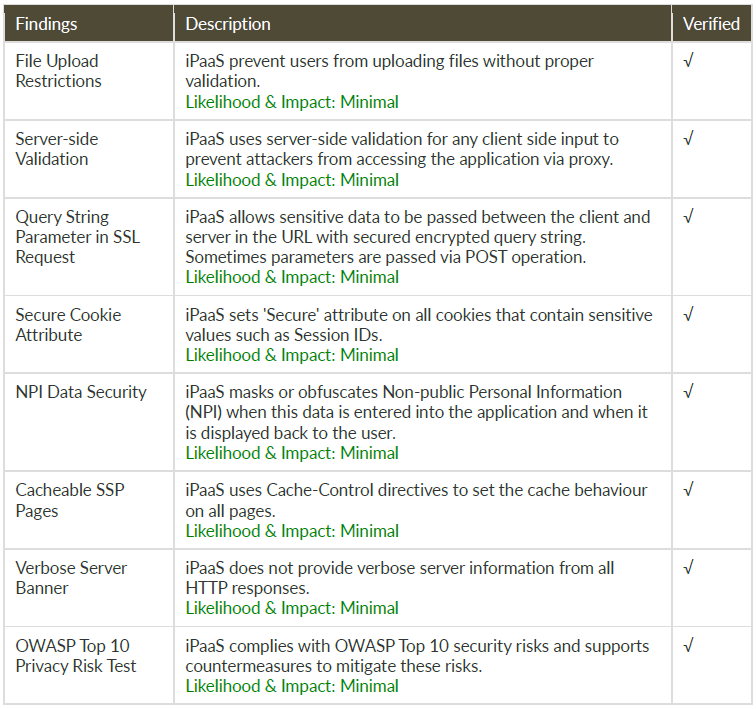
8.2. SECURE BRIDGE
Secure Bridge helps you to securely connect your private databases, MSMQ instances and files from your own secured premises to the iPaaS platform.
8.3. BENEFITS OF SECURE BRIDGE
- Securely connects on premise applications to the cloud applications
- Connects on premise applications running at different locations
- Allows to securely share on premise applications data to other companies
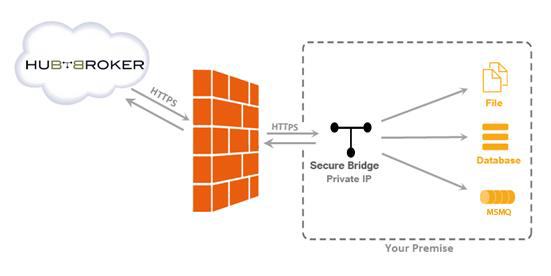
8.4. SECURE ENGINE
Secure Engine helps you to process all your data within your own premise. It also helps you to use your own private servers while using Secure Bridge.
8.5. BENEFITS OF SECURE ENGINE
- Secure Engine provides you with the flexibility of iPaaS while still giving you the opportunity of having your data processed in your secure data center or on premise
- Secure Engine also has Secure Bridge capability
8.6. FINDINGS
9. HOSTING AND INFRASTRUCTURE SECURITY
9.1. MANAGED DEDICATED SERVERS FROM EUKHOST
HubBroker ApS is a valuable customer of eUKhost and its iPaaS application "the iPaaS platform" is hosted on the dedicated server at eUKhost infrastructure.
At eUKhost, they house their servers in highly-secure and ultra-modern Tier 4 data centers in Maidenhead, Reading, Nottingham and Manchester, with BGP network redundancy provided by Simply Transit.
All their data centers are built upon the N+1 principle meaning there is no single point of failure. eUKhost offers a full 100% network uptime guarantee on all servers.
The IT infrastructure that eUKhost provides to its customers is designed and managed in alignment with security best practices and a variety of IT security standards, including:
- SOC1/SSAE16/ISAE3402 (formerly SAS70)
- SOC2
- SOC3
- FISMA
- Fed RAMP
- DODSRG Levels 2 and 4
- PCIDSS Level1
- EU Model Clauses
- ISO9001 /ISO27001 / ISO 27017 / ISO 27018
- ITAR
- IRAP
- FIPS 140-2
- MLPS Level 3
- MTCS
9.2. FINDINGS
Category: Security Policy
Last date of update: 10.10.2019
